Homomorphic Encryption Market: Revolutionizing Secure Data Processing
United States of America– 23 Dec 2025- Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy across industries facing rising cyber threats. This technology addresses key challenges in cloud computing and data analytics, allowing secure processing for sensitive applications. Businesses adopting it gain advantages in compliance and innovation.
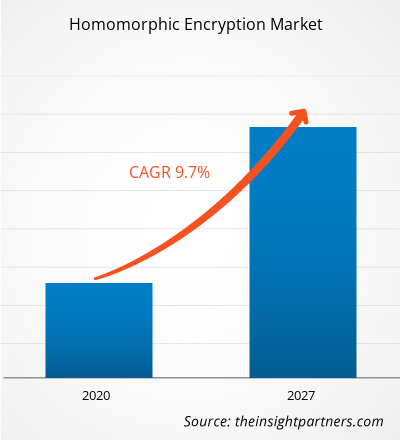
The homomorphic encryption market is expected to reach US$ 246.29 million by 2027, rising from US$ 120.12 million in 2019. The growth rate for revenue curve is estimated to be 9.7%during the forecast period.
For more info-
https://www.theinsightpartners.com/reports/homomorphic-encryption-market
Rising Cyber Threats Drive Adoption
Cyberattacks target financial services, healthcare, and government sectors, exposing vulnerabilities during data storage, transmission, and analysis. Traditional encryption requires decryption for processing, creating risks on open platforms and cloud environments. Homomorphic encryption maintains data security throughout operations, enabling robust protection without disrupting workflows.
Organizations shift vast data volumes through networks, amplifying breach risks. Governments emphasize consumer data protection amid misuse concerns, accelerating this technology's rollout. Industries vulnerable to threats prioritize solutions balancing security and functionality.
For deeper insights, Download PDF Copy-
https://www.theinsightpartners.com/sample/TIPRE00014748
Cloud Computing Fuels Demand
Cloud adoption surges due to cost savings, scalability, and flexibility, but raises database security issues. Standard encryption fails during computations, as data must decrypt first, exposing it to risks. Homomorphic encryption performs complex calculations on encrypted data, ideal for secure cloud analytics.
Enterprises leverage cloud for disaster recovery and mobility, demanding privacy-preserving tools. This integration supports encrypted machine learning and AI-driven insights without compromising confidentiality. Providers optimize for multi-tenant environments, enhancing trust in remote processing.
Homomorphic Encryption Market: Revolutionizing Secure Data Processing
United States of America– 23 Dec 2025- Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy across industries facing rising cyber threats. This technology addresses key challenges in cloud computing and data analytics, allowing secure processing for sensitive applications. Businesses adopting it gain advantages in compliance and innovation.
The homomorphic encryption market is expected to reach US$ 246.29 million by 2027, rising from US$ 120.12 million in 2019. The growth rate for revenue curve is estimated to be 9.7%during the forecast period.
For more info- https://www.theinsightpartners.com/reports/homomorphic-encryption-market
Rising Cyber Threats Drive Adoption
Cyberattacks target financial services, healthcare, and government sectors, exposing vulnerabilities during data storage, transmission, and analysis. Traditional encryption requires decryption for processing, creating risks on open platforms and cloud environments. Homomorphic encryption maintains data security throughout operations, enabling robust protection without disrupting workflows.
Organizations shift vast data volumes through networks, amplifying breach risks. Governments emphasize consumer data protection amid misuse concerns, accelerating this technology's rollout. Industries vulnerable to threats prioritize solutions balancing security and functionality.
For deeper insights, Download PDF Copy- https://www.theinsightpartners.com/sample/TIPRE00014748
Cloud Computing Fuels Demand
Cloud adoption surges due to cost savings, scalability, and flexibility, but raises database security issues. Standard encryption fails during computations, as data must decrypt first, exposing it to risks. Homomorphic encryption performs complex calculations on encrypted data, ideal for secure cloud analytics.
Enterprises leverage cloud for disaster recovery and mobility, demanding privacy-preserving tools. This integration supports encrypted machine learning and AI-driven insights without compromising confidentiality. Providers optimize for multi-tenant environments, enhancing trust in remote processing.