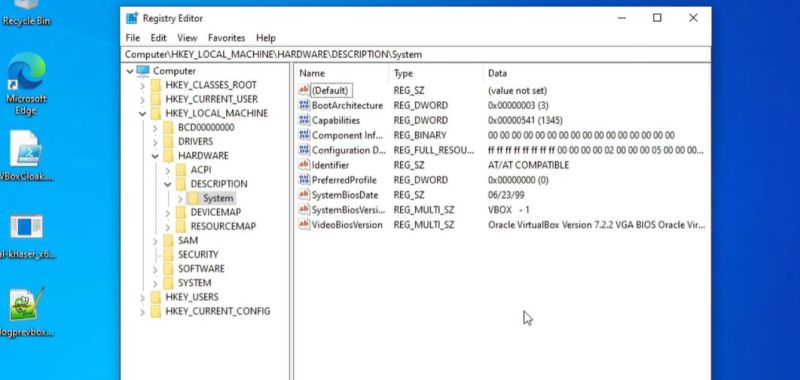
Ever wondered how malware can tell if it’s being run in a virtual machine?
In the article "Making a Virtual Machine Look like Real Hardware to Malware," we explore the challenges of analyzing suspicious software safely. While using a virtual machine (VM) seems like a smart way to identify harmful code, malware has developed tactics to detect these environments, making it tougher for security enthusiasts to stay ahead of the game.
This brings to mind the importance of continually adapting our defensive strategies in the ever-evolving landscape of cybersecurity. As technology advances, so do the threats we face.
Are we doing enough to outsmart these sophisticated attacks?
Read more here: https://hackaday.com/2025/10/27/making-a-virtual-machine-look-like-real-hardware-to-malware/
#Cybersecurity #Malware #VirtualMachine #TechTrends #SecurityAwareness
In the article "Making a Virtual Machine Look like Real Hardware to Malware," we explore the challenges of analyzing suspicious software safely. While using a virtual machine (VM) seems like a smart way to identify harmful code, malware has developed tactics to detect these environments, making it tougher for security enthusiasts to stay ahead of the game.
This brings to mind the importance of continually adapting our defensive strategies in the ever-evolving landscape of cybersecurity. As technology advances, so do the threats we face.
Are we doing enough to outsmart these sophisticated attacks?
Read more here: https://hackaday.com/2025/10/27/making-a-virtual-machine-look-like-real-hardware-to-malware/
#Cybersecurity #Malware #VirtualMachine #TechTrends #SecurityAwareness
Ever wondered how malware can tell if it’s being run in a virtual machine? 🤔
In the article "Making a Virtual Machine Look like Real Hardware to Malware," we explore the challenges of analyzing suspicious software safely. While using a virtual machine (VM) seems like a smart way to identify harmful code, malware has developed tactics to detect these environments, making it tougher for security enthusiasts to stay ahead of the game.
This brings to mind the importance of continually adapting our defensive strategies in the ever-evolving landscape of cybersecurity. As technology advances, so do the threats we face.
Are we doing enough to outsmart these sophisticated attacks?
Read more here: https://hackaday.com/2025/10/27/making-a-virtual-machine-look-like-real-hardware-to-malware/
#Cybersecurity #Malware #VirtualMachine #TechTrends #SecurityAwareness
·2K Views
·0 Reviews