Mobile Data Protection Market Size, Share, Trends, and Forecast 2025–2031
The Mobile Data Protection Market is expanding rapidly as organizations prioritize securing sensitive data on mobile devices amid rising cybersecurity threats. This growth reflects the critical need for advanced solutions in an era of widespread mobile usage for business and personal activities.
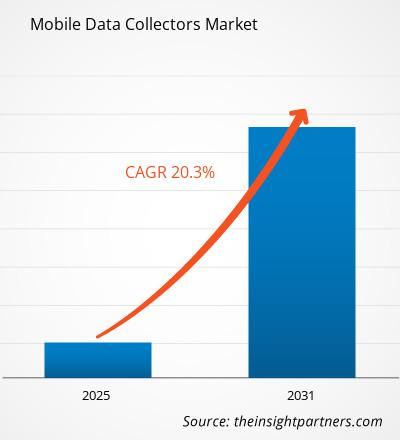
The Mobile Data Protection Market size is expected to reach US$ 4.41 Billion by 2031. The market is anticipated to register a CAGR of 10.9% during 2025-2031.
Read More-
https://www.theinsightpartners.com/reports/mobile-data-protection-market
Key Market Drivers
Rising cybersecurity threats, including phishing, malware, and data breaches, propel demand for mobile data protection technologies like encryption and remote wipe capabilities. Proliferation of Bring Your Own Device (BYOD) policies introduces vulnerabilities by blending personal and corporate data, compelling enterprises to adopt robust security measures for compliance and risk mitigation.
Segmentation Insights
The market divides into components such as software and services, with deployment options spanning on-premise and cloud-based systems. Enterprise sizes range from SMEs, which lead due to digital transformation needs, to large enterprises requiring scalable protections. Industry verticals like BFSI, healthcare, IT and telecom, and retail drive adoption, as these sectors handle highly sensitive information vulnerable to mobile exploits.
Emerging Trends
Integration with Mobile Threat Defense (MTD) solutions enables real-time threat detection against malware and unsafe networks, enhancing overall device security. Cloud-based platforms gain traction for their flexibility, remote management, and centralized policy enforcement, simplifying IT oversight in hybrid work environments. AI and machine learning introduce proactive anomaly detection, automating responses to potential breaches before impact.
Download PDF Copy-
https://www.theinsightpartners.com/sample/TIPRE00003305
Regional Dynamics
North America dominates due to advanced digital infrastructure and stringent regulations, while Asia-Pacific accelerates with smartphone proliferation and remote work trends in countries like China and India. Europe emphasizes compliance with data privacy laws, fostering innovation in endpoint security. Emerging markets in Middle East & Africa and Latin America present opportunities as mobile adoption surges without proportional security investments.
Challenges and Opportunities
Managing diverse mobile platforms and devices poses complexity, particularly for SMEs lacking expertise, while regulatory fragmentation in emerging regions hinders uniform adoption. Opportunities abound in healthcare and financial sectors needing HIPAA and GDPR-compliant tools, alongside AI-driven defenses for predictive threat intelligence. Vendors focusing on zero-trust models and containerization for apps can capture growth in IoT-integrated environments.
Leading Players
Key providers include Check Point Software Technologies, Microsoft Corporation, Dell Technologies, Symantec (Broadcom), Hewlett Packard Enterprise, McAfee, Sophos, Trend Micro, Cisco Systems, and Gemalto. These firms innovate through cloud integrations, biometric authentication, and endpoint solutions to address evolving threats.
Future Outlook
The market evolves toward comprehensive endpoint security, with zero-trust architectures and mobile app containerization becoming standard. As remote work and IoT expand, solutions emphasizing behavioral analytics and blockchain for tamper-proof records will define leadership. Organizations investing now position themselves against sophisticated attacks, ensuring data integrity across global operations.
Mobile Data Protection Market Size, Share, Trends, and Forecast 2025–2031
The Mobile Data Protection Market is expanding rapidly as organizations prioritize securing sensitive data on mobile devices amid rising cybersecurity threats. This growth reflects the critical need for advanced solutions in an era of widespread mobile usage for business and personal activities.
The Mobile Data Protection Market size is expected to reach US$ 4.41 Billion by 2031. The market is anticipated to register a CAGR of 10.9% during 2025-2031.
Read More- https://www.theinsightpartners.com/reports/mobile-data-protection-market
Key Market Drivers
Rising cybersecurity threats, including phishing, malware, and data breaches, propel demand for mobile data protection technologies like encryption and remote wipe capabilities. Proliferation of Bring Your Own Device (BYOD) policies introduces vulnerabilities by blending personal and corporate data, compelling enterprises to adopt robust security measures for compliance and risk mitigation.
Segmentation Insights
The market divides into components such as software and services, with deployment options spanning on-premise and cloud-based systems. Enterprise sizes range from SMEs, which lead due to digital transformation needs, to large enterprises requiring scalable protections. Industry verticals like BFSI, healthcare, IT and telecom, and retail drive adoption, as these sectors handle highly sensitive information vulnerable to mobile exploits.
Emerging Trends
Integration with Mobile Threat Defense (MTD) solutions enables real-time threat detection against malware and unsafe networks, enhancing overall device security. Cloud-based platforms gain traction for their flexibility, remote management, and centralized policy enforcement, simplifying IT oversight in hybrid work environments. AI and machine learning introduce proactive anomaly detection, automating responses to potential breaches before impact.
Download PDF Copy- https://www.theinsightpartners.com/sample/TIPRE00003305
Regional Dynamics
North America dominates due to advanced digital infrastructure and stringent regulations, while Asia-Pacific accelerates with smartphone proliferation and remote work trends in countries like China and India. Europe emphasizes compliance with data privacy laws, fostering innovation in endpoint security. Emerging markets in Middle East & Africa and Latin America present opportunities as mobile adoption surges without proportional security investments.
Challenges and Opportunities
Managing diverse mobile platforms and devices poses complexity, particularly for SMEs lacking expertise, while regulatory fragmentation in emerging regions hinders uniform adoption. Opportunities abound in healthcare and financial sectors needing HIPAA and GDPR-compliant tools, alongside AI-driven defenses for predictive threat intelligence. Vendors focusing on zero-trust models and containerization for apps can capture growth in IoT-integrated environments.
Leading Players
Key providers include Check Point Software Technologies, Microsoft Corporation, Dell Technologies, Symantec (Broadcom), Hewlett Packard Enterprise, McAfee, Sophos, Trend Micro, Cisco Systems, and Gemalto. These firms innovate through cloud integrations, biometric authentication, and endpoint solutions to address evolving threats.
Future Outlook
The market evolves toward comprehensive endpoint security, with zero-trust architectures and mobile app containerization becoming standard. As remote work and IoT expand, solutions emphasizing behavioral analytics and blockchain for tamper-proof records will define leadership. Organizations investing now position themselves against sophisticated attacks, ensuring data integrity across global operations.